Why Choose Torzon Market?
Torzon Market. The name you keep hearing about. Why? Simple. It works. Since 2022, the platform has processed thousands of orders. Zero major security breaches. 99.8% uptime. These numbers speak louder than marketing talk.
What makes Torzon Market different from other darknet marketplaces? Three things:
- Real encryption - AES-256 for data, ChaCha20 for transport. Not buzzwords. Actual protection.
- Mandatory 2FA - No optional security here. Every Torzon account requires two-factor authentication.
- XMR-first approach - Monero payments preferred. Bitcoin accepted but XMR recommended for maximum privacy.
- Active anti-phishing - Our mirror verification system catches fake sites before you do.
The team understands something basic: privacy is not a feature. It's the foundation. Every line of code, every server configuration, every policy decision starts with one question. Does this protect the user? If not, it doesn't ship.
Torzon Market Security Architecture
How does Torzon keep your data safe? Let's break it down. No jargon. Just facts.
First layer: network security. All our servers run behind Tor. No clearnet exposure. Traffic analysis? Good luck. The onion routing makes correlation attacks impractical. Add our custom timing obfuscation and you've got serious protection against even state-level adversaries.
Second layer: application security. This marketplace code undergoes regular audits. Found a bug? Our bug bounty program pays well. White hats have tested it Market extensively. The codebase is tight.
Third layer: operational security. The the team practices what we preach. Compartmentalized access. Air-gapped systems for critical operations. No single point of failure. If one component fails, the marketplace keeps running.
Torzon Marketplace Features That Matter
Forget feature lists that go on forever. Here's what the marketplace users actually care about:
- Escrow that works - Funds locked until you confirm delivery. Disputes resolved fairly. Period.
- Vendor verification - Every vendor posts a bond. Scammers lose money. Good vendors thrive.
- PGP everywhere - Messages encrypted by default on the marketplace. Your communications stay private.
- Mirror redundancy - Multiple our onion links always available. DDoS? We stay online.
Getting Started on the marketplace
New to Torzon? Here's the quick version. Download Tor Browser from torproject.org. Only from there. Nowhere else. Got it? Good. Check our complete access guide for detailed instructions.
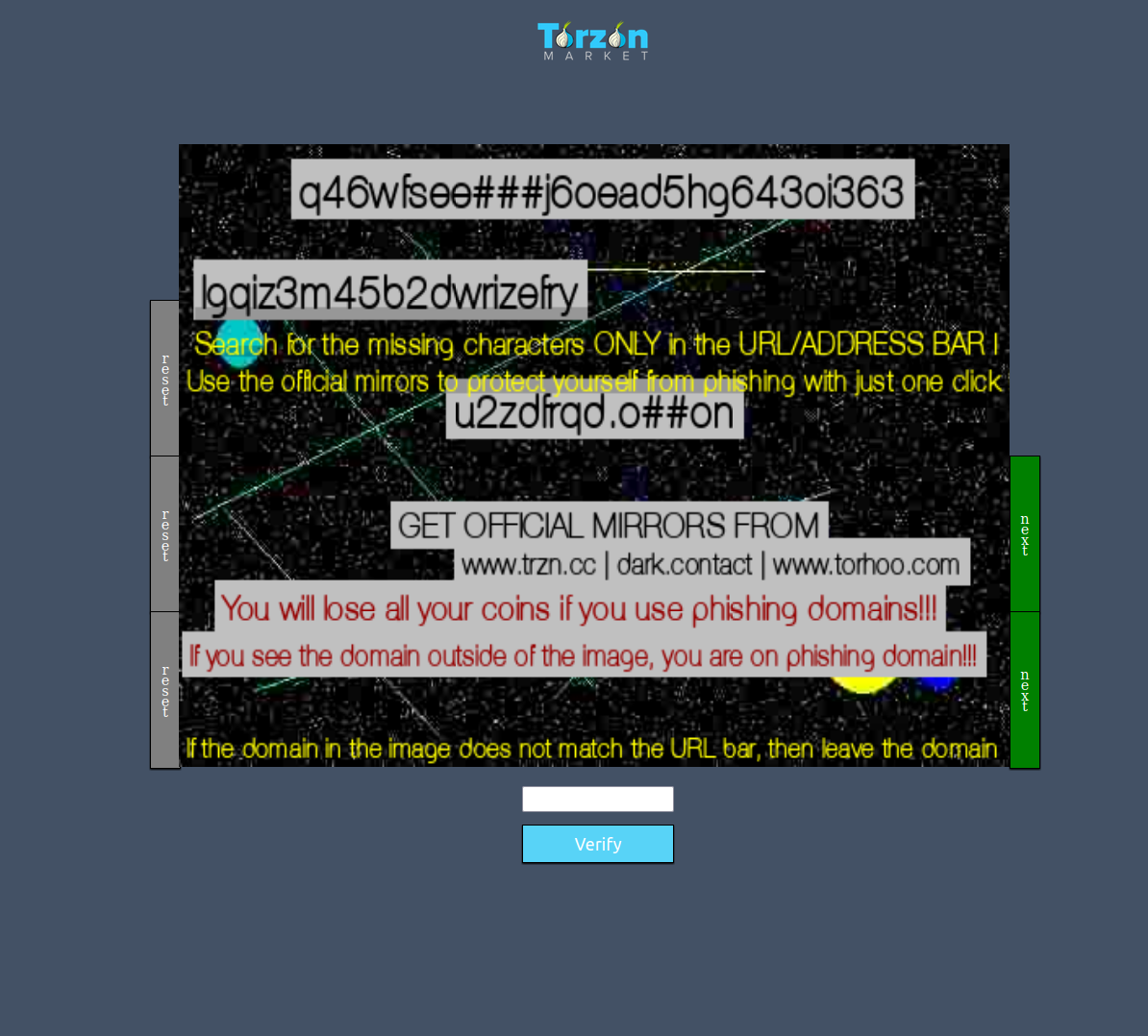
Next, find a verified official link. Use our official mirror page. Bookmark it. Never trust random forum links. Phishing sites look identical to the marketplace. The only difference? They steal your credentials.
Create your Torzon account. Strong password. Unique username. Set up 2FA immediately. Write down your mnemonic phrase. Store it offline. Paper works. Metal plates work better. Digital backups? Bad idea. Read our FAQ section for more security tips.
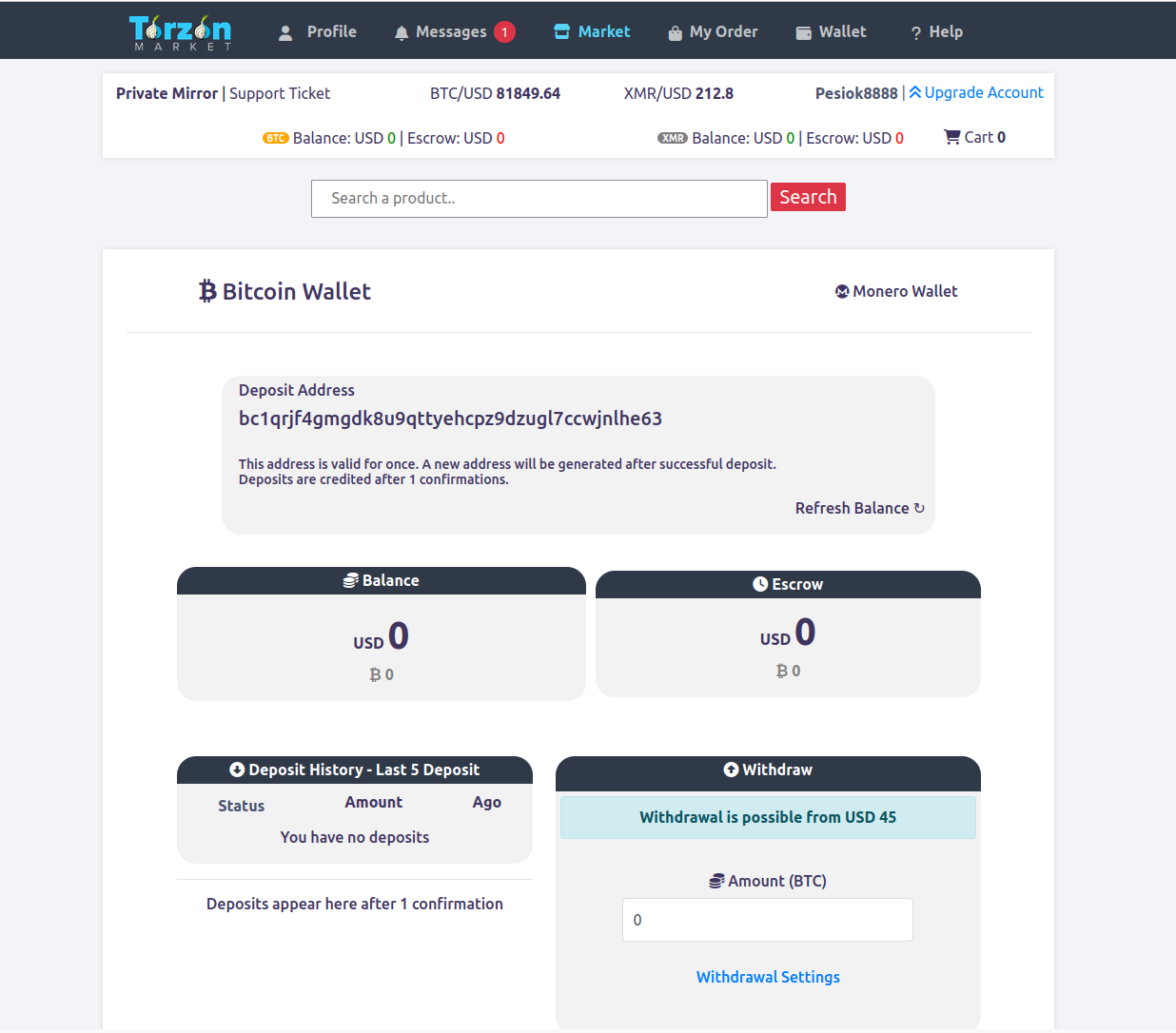
Fund your wallet. XMR preferred. If using BTC, run it through a mixer first. Your bank shouldn't know about your marketplace activity. Neither should blockchain analysts. Learn more about our platform.
Torzon Market Community
A marketplace is only as good as its community. The marketplace has built something special. Verified vendors with years of reputation. Buyers who leave honest reviews. Moderators who actually respond. Support tickets answered within 24 hours. Usually faster.
The Torzon forum is active. Questions get answers. Scam reports get investigated. New vendors get vetted. This isn't some abandoned marketplace. Torzon Market lives and breathes.
Want proof? Check the stats. Daily active users in the thousands. New listings every hour. Transaction volume growing month over month. The marketplace isn't going anywhere.